Archive
Don’t worry. There is no spying occuring!
Just a quick post to clear something up.
Site stats have shown lots of interest from this post;
http://community.bt.com/t5/BT-Infinity/usa-department-of-defense-spying-on-infinity-users/td-p/578197
Which seems related to this post;
http://forums.thinkbroadband.com/fibre/4107499-alert-in-modem-log.html
Just to clear up any confusion, the following address ranges are private;
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
That is, you can’t use them on ‘The Internet’, they belong only in private home/business/management networks behind a real public IP (such as your home 192.168.0.x network behind one real internet IP).
The network I have discussed is a private network, it’s internal to the Infinity network, it’s directly attached (via the 301 VLAN) to your devices.
The reason it’s registered to the US DoD in ‘Who Is’ lookups is historic and dates back to Arpa-net. It’s the same historic stuff as why your IPv4 reverse DNS PTR records all end in ‘in-addr.arpa’
Further reading;
https://en.wikipedia.org/wiki/Private_network
It has (and let me be quite clear here before this blog attracts more attention that it ever wanted) NOTHING TO DO with the USA or related parties doing ANYTHING to BT Infinity connections or data.
That is all.
On an unrelated note however, the IPS logs in the second link are quite interesting from the perspective of return SNMP traffic, more later!
BGP / MPLS Routers on Infinity TR069 Network
Following on from the previous post, the extra VLAN provided to each customers CPE can be bridged through to the secondary ethernet port, allowing any computer to receive an IP address on the management network via DHCP.
Obviously I wanted to know how far-reaching this network goes that is getting pushed into every customers premises.
First thing first, the access subnet only allows communication between your CPE and the subnet gateway, which is a lot better than seeing a sea of other CPE’s from a security standpoint.
TR069 Server
So the CPE doesnt seem to have a TR069 URL and there is no extra information in the DHCP lease, so I haven’t looked for/at the TR069 server.
However, available details from the CPE device are;
ACS URL: Blank
ACS USER: hgw
ACS PW: ❤ chars>
CONNECTION REQUEST USER: acs
CONNECTION REQUEST PASS: ❤ chars>
CERT ENABLE: no
PERIODIC INFORM: no
DNS Servers
I was given two DNS servers;
10.160.170.231
10.160.170.232
These look to be running a stable, well patched version of Bind but I didn’t probe any deeper as this is journey is for understanding the infrastructure ONLY, not for causing issues or poor technicians any extra work!
Routes
On the way to our DNS servers we pass a couple of hops;
[root@box ~]# tracepath 10.160.170.232
1: 30.4x.x.me 0.119ms pmtu 1500
1: 30.4x.x.x 5.924ms asymm 2
2: 10.160.160.65 13.684ms asymm 3
3: no reply
4: no reply[root@box ~]# tracepath 10.160.170.231
1: 30.4x.x.me 0.107ms pmtu 1500
1: 30.4x.x.x 5.954ms asymm 2
2: 10.160.160.65 13.699ms asymm 3
3: no reply
4: no reply
This got me thinking, what else is on 10.160.170.231; Nothing.
Further thinking, 10.160.160.x, 10.160.170.x, followed the pattern, some 10.160.x.0/24 subnets come back as routable, while some give dest net unreachable.
Creating a list of routable nets starting 10.160.x.0/24 seemed wise;
[root@box ~]# for i in $(seq 1 254) ; do ping -t 1 -c 1 10.160.$i.1 | grep -B 1 “Destination Net Unreachable” ; done | grep PING | sort | uniq | awk -F “.” ‘{print $3}’ | sort -n > notvalid.txt
[root@box ~]# seq 1 255 > all.txt
[root@box ~]# diff notvalid.txt all.txt | grep “>” | cut -c 3-6
In this CLI mess above, we are finding a list of 10.160.x subnets that Don’t have a route (Destination Net Unreachable). and inverting it to give us a list of valid nets.
BGP / MPLS Devices
So what’s on the routable subnets? Looks like BGP/MPLS routers, as SSH, BGP and LDP (Label distribution protocol) services are available;
Host is up (0.014s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
179/tcp open bgp
646/tcp open ldp10.160.128.67
Host is up (0.012s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
179/tcp open bgp
646/tcp open ldp10.160.160.66
Host is up (0.011s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
179/tcp open bgp
646/tcp open ldp
This is my stop
If this were my network, my next thoughts would be;
– BGP requires configuration on both sides to bring up a peer but LDP doesn’t have any such security and allows directed creation of sessions even on different IP subnets.
– a successful LDP session may give information as to surrounding routers and networks.
– SSH could have weak passwords
But, this ISN’T my network and as this was merely a quick look into the VLAN’s presented in the premises, I’m not going to risk (for legal and ethical reasons) bringing up an LDP session or trying the SSH connection.
Hopefully someone BT-related could fill in this picture with what we are looking at here?
Anyway, wasn’t expecting open BGP/LDP ports a hop away from any users CPE!
BT Infinity TR069 VLAN Access
Looking at the Customer Premise Equipment with a standard BT Infinity installation, we have;
The BT Home Hub 3
This isn’t really that interesting for looking at the infinity network, it’s a NAT router with WiFi that gets it’s internet connectivity via an Ethernet port and authenticates via PPPoE.
We’ll leave it there for the home hub, we’re more interested in the device that sits between the home hub and the BT wall socket, the re-badged Huawei HG612 VDSL router.
Huawei HG612
This device is used to bridge the VDSL link (Layer 1/2 protocol on which connectivity is delivered to the premise) to the Ethernet link into the home hub (or any other router for that matter).
The device is the demarcation point for BT Openreach’s service (who provide the VDSL infrastructure branded by BT as infinity) and probably belongs to BT Openreach even though it’s in your premise. (can someone confirm this?).
The device arrives with the Openreach engineer when the service is installed and is locked down with a custom firmware to provide only one customer-facing action, a bridge between the VDSL connection and an Ethernet port to the homehub. Authentication credentials are set on the homehub/router and also passed through the HG612 to the external infinity infrastructure via PPTP.
Anyway, enough background information. There are many places on the web already covering these devices in detail and we just don’t care that much within the scope of this post.
Getting more information from the HG612
So I started looking for more information from the configuration of this device and found that unofficial firmware has already been released; driven it seems by users wanting VDSL statistics from the device which the current firmware doesn’t provide. In-fact by default it provides no user portal/access and is meant to be a black box behind your homehub that you ignore.
Updating/unlocking this device to access it’s functionality is out of scope of this post, information can be found here;
Click to access hg612_unlock_instructions_v1-3.pdf
Looking around the HG612 configuration
So, DSL stats are fine, cacti will be happy, you’ll be interested in your new graphs for a couple of minutes, then once you’re bored; what else is there?
So, this is what I was interested in;
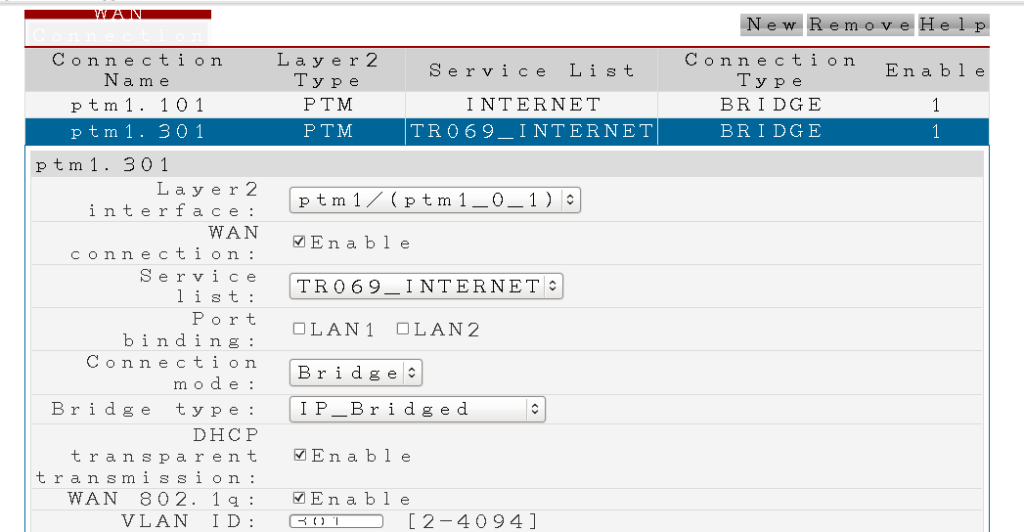
PTM (Packet transfer mode) is an encapsulation method supported on VDSL2 allowing the transport of IP, PPP, Ethernet or MPLS packets over the DSL link instead of using ATM. It’s based on EFM (first mile ethernet IEEE802.3ah).
We see there are two Ethernet VLAN’s being presented down the VDSL PTM link, one which gets bridged directly through to the internal ‘LAN1’ port on the Huawei device. This is our internet connection, which gets tagged with VLAN tag 101 on the PTM link.
However, there is another connection, VLAN301, which terminates on the Huawei device itself; If you click around the Huawei web interface, you’ll find a DHCP client expects to get an IP address from this VLAN, providing a control network for the HG216 to run TR-069 autoconfiguration.
https://en.wikipedia.org/wiki/TR-069
Because the existing PTM1.301 interface isnt a bridge it’s IP terminated, I couldn’t find any way of bridging this VLAN directly to a laptop via the ‘unused’ LAN2 port (that you’ll be familiar with if you’ve updated the firmware on your Huawei device, as it’s this port that is configured on 192.168.1.1/24 for the web interface and telnet access).
However, it can be done through the CLI;
using brctl command after logging in via telnet and typing ‘shell’, you can end up with the PTM1.301 interface bridged to the physical LAN2 port.
Connected to 192.168.1.1.
Escape character is ‘^]’.Welcome Visiting Huawei Home Gateway
Copyright by Huawei Technologies Co., Ltd.
Login:admin
Password:
ATP>shellBusyBox v1.9.1 (2010-10-15 17:59:06 CST) built-in shell (ash)
Enter ‘help’ for a list of built-in commands.# brctl show
bridge name bridge id STP enabled interfaces
br0 8000.XXXXXXXXXXXX no eth0.2
eth0.3
eth0.4
ptm1.301
br1 8000.XXXXXXXXXXXX ptm1.101
eth0.5
#
ATP>
So, laptop connected to LAN2, dhclient;
[root@box ~]# dhclient eth0
[root@box ~]# ip addr list
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff
inet 30.4x:xx:xx/21 brd 30.4x:xx:xx scope global eth0
inet6 fe80::xxx:xxx:xx:xx:xx:xxx/64 scope link
valid_lft forever preferred_lft forever
Excellent, IP address in 30.4x.xx.xx/21 range with two nameservers and a default gateway.
You can dhclient the VLAN301 IP and still also manually set a 192.168.1.2/24 IP to keep your access to the management interface of the HG612 (of course).
Thats all for now, seems interesting.
Welcome
Hi, This little corner of wordpress is to document information i’ve come across while investigating a home BT Infinity / Infinity 2 connection now available in the UK.
I hope this will provide some feedback from others or inspire others to investigate such a new infrastructure.
Probably need to say this, so i’ll get it out of the way; The information provided here is my own, has had no involvement from others, corporate or otherwise. All thoughts and information expressed here are my own.
Information posted here is for academic interest only and should not be used in any other way.
